By Yann Albou.

What is a Supply Chain Attack, how to best protect yourself and what are the technical solutions for our CI/CD in a DevSecOps approach. In this series of articles we will present the concepts and discuss the aspects close to development, the continuous integration and continuous delivery part, as well as the operational aspects.
Historically our security was mainly centered on a perimeter defense with the representation of the wall of a castle. Just as a castle is built to resist external attacks, a company implements security measures to protect its computer network from cyberattacks.
Today the attack vectors are multiplying and not necessarily on the most visible elements.
Attackers can circumvent this wall using a supply chain type attack. They will then seek to break into the network by exploiting vulnerabilities in the software or equipment provided by third-party suppliers. Just as castle attackers seek to find a crack in the wall to break in, attackers seek to exploit a vulnerability in part of the supply chain to break into the corporate network.
Thus, to ensure optimal security, the company must not only strengthen its own wall, but also monitor and secure its entire supply chain, ensuring that its suppliers respect the same standards of security and confidentiality than the company itself.
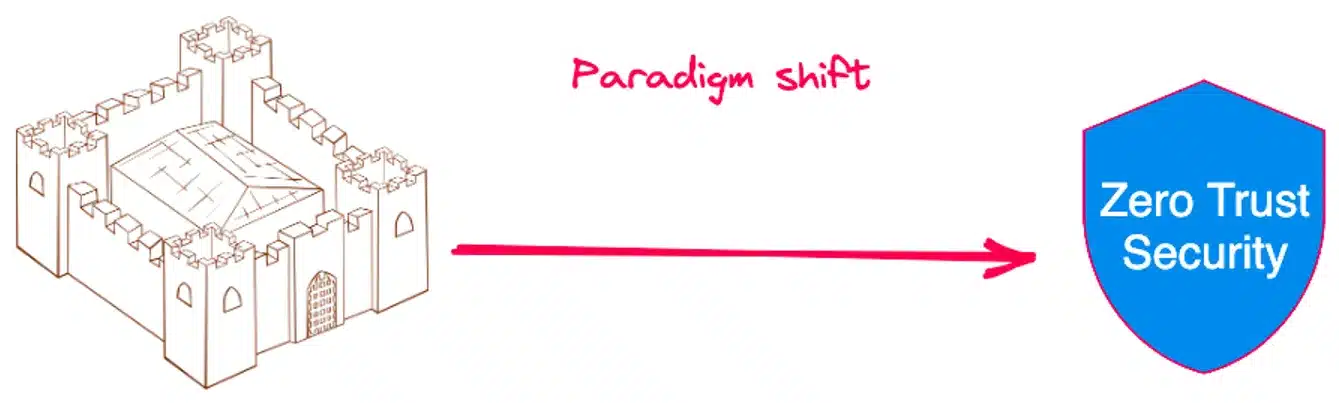
We have moved from perimeter security to so-called “zero trust” security: Security applies to all of IT, not just the network but also identity, data, infrastructure, applications , … and the supply chain!
A supply chain attack is a cyberattack that seeks to harm an organization by targeting the least secure elements of the supply chain.
The impacts on the supply chain are of various kinds:
Here are a number of more or less recent examples of this type of attack:
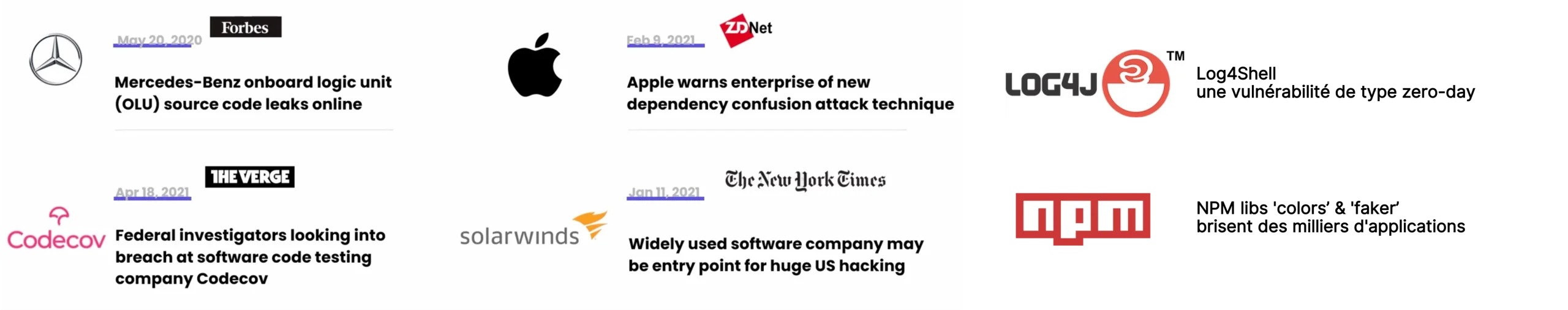
The Log4J example is interesting: This vulnerability called Log4shell (CVE-2021-44228) is zero-day involving the execution of arbitrary code. It has affected thousands of organizations and continues to do so because 1 year after this vulnerability, 30% of downloads still concerned versions affected by this problem!
The NPM case with the ‘colors’ & ‘faker’ libs is also very interesting because it was the developer who voluntarily introduced bugs and thus impacted thousands of applications. This case is complex to judge because it involves the eternal question of open source and its maintainability, but must raise questions about how to use our dependencies.
Through these few examples, which are multiplying, we see that it is increasingly important, even vital, to protect your software factory and the way in which we deliver our applications.
The target now becomes: Any supplier that relies on third parties to manufacture a product is vulnerable to supply chain attacks
The question is therefore how to protect yourself as much as possible against this type of attack and what are the best practices related to DevSecOps.
In this series of articles we will present some of these best practices with a focus on security in the Software Factory but we will not cover:
This will be a set of non-exhaustive recommendations based on our feedback.
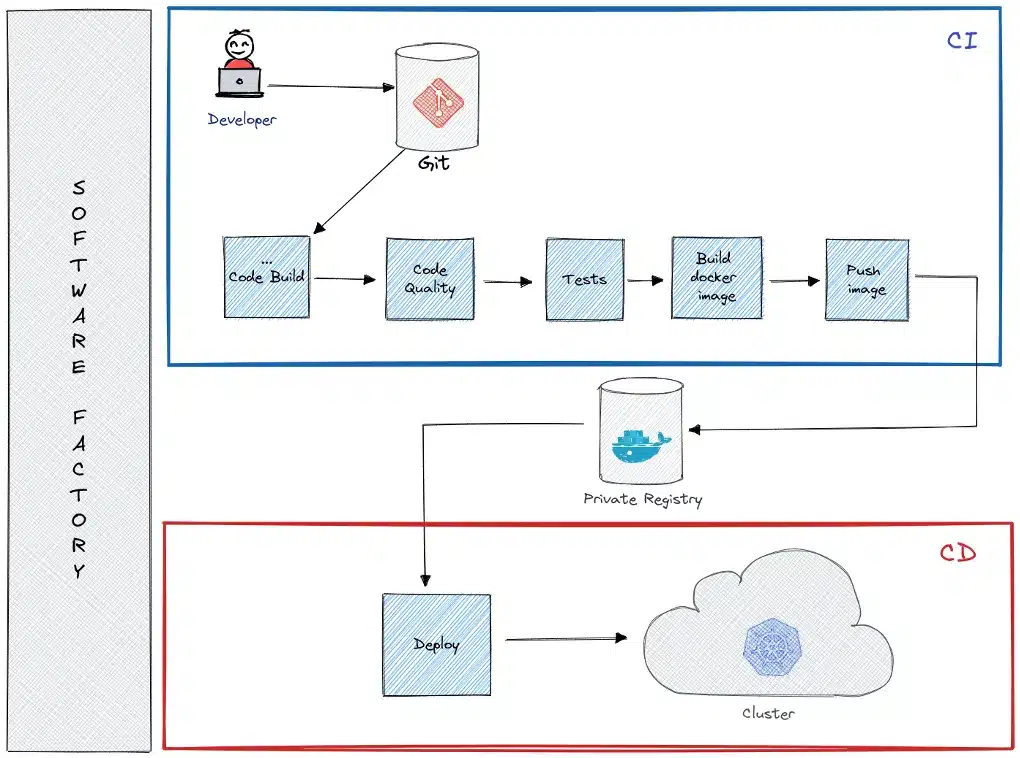
Most of you already know what CI/CD (Continuous Integration / Continuous Delivery) is and the principles of automation, testability, quality, repeatability of build and deployment,… The purpose of this series of articles is not to describe these principles.
However, we will zoom in on several points of this chain by providing specific recommendations related to security, starting with:
In order to facilitate the application of our recommendations, we have adopted a signage:
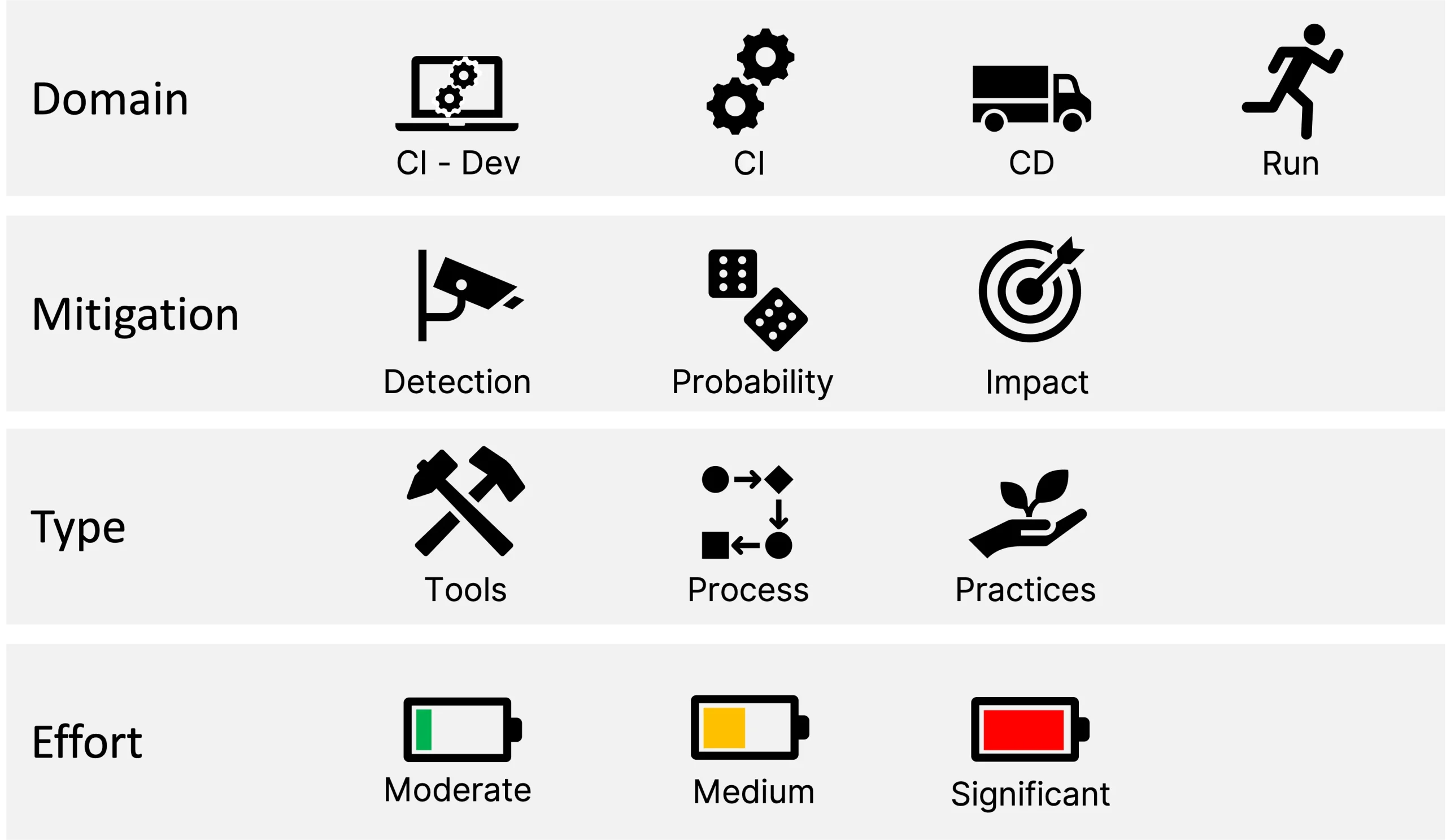
It will allow you to indicate:
With Fabrice Vergnenègre we presented this topic on a 45m format at DevOps-D Day Marseille of which here is the video:
In the next articles we will discuss the different solutions to protect ourselves as much as possible from this type of attack.
In particular, we will address the following topics:
This is not an exhaustive list of good practices because they are constantly evolving and new threats emerge regularly.
But all of these themes improve the security of your Software Factory to be part of a DevSecOps approach where the development, operational and security teams work together effectively to make all the actions around the software supply chain.